先自我介绍一下,小编浙江大学毕业,去过华为、字节跳动等大厂,目前阿里P7
深知大多数程序员,想要提升技能,往往是自己摸索成长,但自己不成体系的自学效果低效又漫长,而且极易碰到天花板技术停滞不前!
因此收集整理了一份《2024年最新网络安全全套学习资料》,初衷也很简单,就是希望能够帮助到想自学提升又不知道该从何学起的朋友。






既有适合小白学习的零基础资料,也有适合3年以上经验的小伙伴深入学习提升的进阶课程,涵盖了95%以上网络安全知识点,真正体系化!
由于文件比较多,这里只是将部分目录截图出来,全套包含大厂面经、学习笔记、源码讲义、实战项目、大纲路线、讲解视频,并且后续会持续更新
如果你需要这些资料,可以添加V获取:vip204888 (备注网络安全)

正文
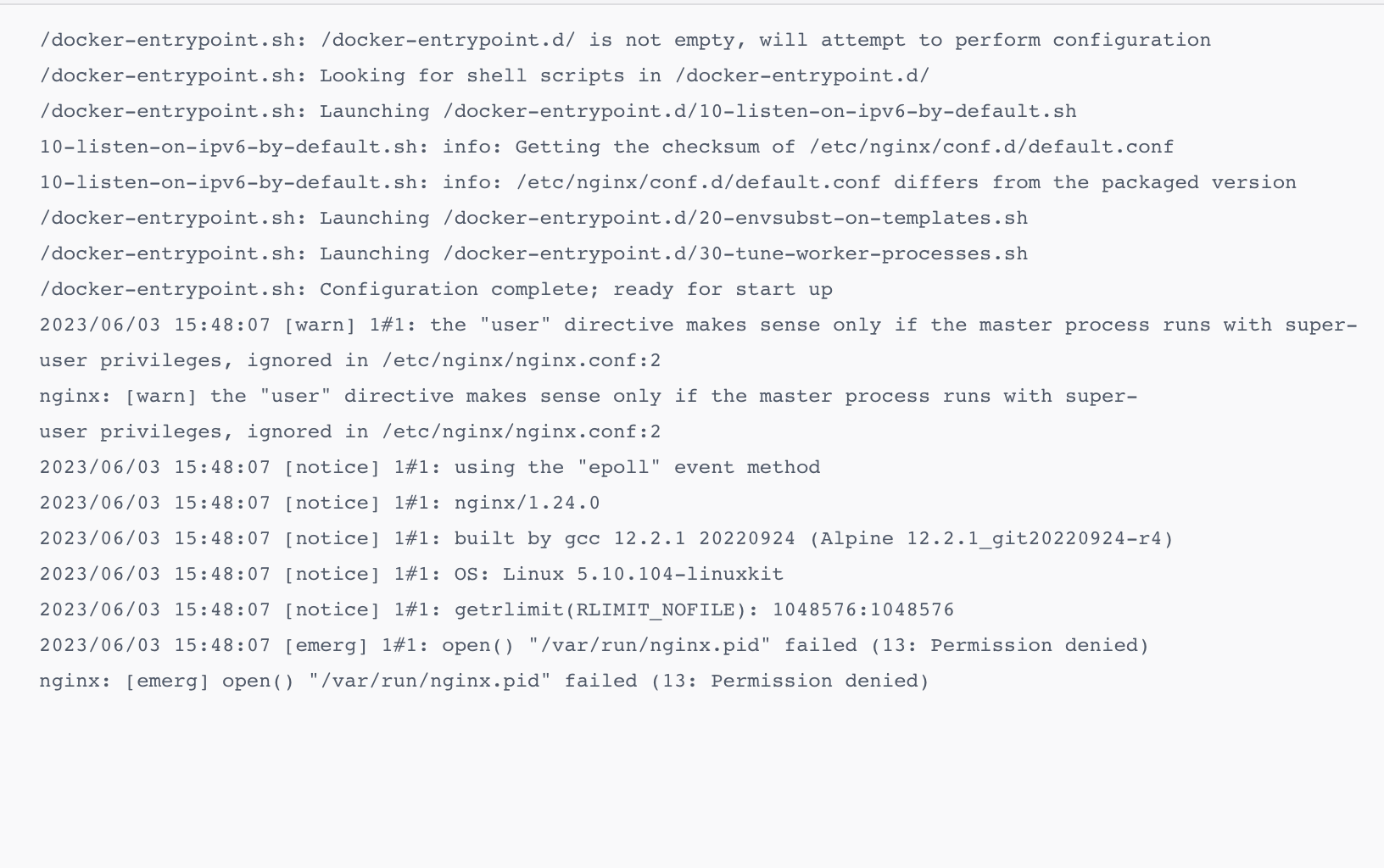
2023/06/03 15:48:07 [emerg] 1#1: open() “/var/run/nginx.pid” failed (13: Permission denied)
nginx: [emerg] open() “/var/run/nginx.pid” failed (13: Permission denied)
##### 尝试2: 在容器中装sudo, 在docker容器中使用非root用户修改/etc/hosts文件,失败告终
…此处省略一些基础代码
RUN adduser -D appuser
USER appuse
下面的代码没有起作用,请路过的小伙伴不吝赐教,/app/setup/hosts 是ip hostname 对应关系的文件
RUN apk add sudo
RUN sudo chmod 777 /etc/hosts;
RUN cat /app/setup/hosts >> /etc/hosts;
RUN sudo /bin/chmod 644 /etc/hosts;
EXPOSE 80
CMD [“nginx”, “-g”, “daemon off;”]
##### 尝试3:先创建新用户,然后使用chown添加权限,部分失败告终
…此处省略一些基础代码
RUN adduser -D appuser
RUN chown -R appuser /var/cache
RUN chown -R appuser /etc/nginx
下面的/ var/run 代码没有起作用,请路过的小伙伴不吝赐教
RUN chown -R appuser /var/run
USER appuser
RUN chmod -R 755 /etc/nginx
RUN chmod -R 755 /var/cache
RUN chmod -R 755 /var/run
EXPOSE 80
CMD [“nginx”, “-g”, “daemon off;”]
报错如下:
/docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration
/docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/
/docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh
10-listen-on-ipv6-by-default.sh: info: Getting the checksum of /etc/nginx/conf.d/default.conf
10-listen-on-ipv6-by-default.sh: info: /etc/nginx/conf.d/default.conf differs from the packaged version
/docker-entrypoint.sh: Launching /docker-entrypoint.d/20-envsubst-on-templates.sh
/docker-entrypoint.sh: Launching /docker-entrypoint.d/30-tune-worker-processes.sh
/docker-entrypoint.sh: Configuration complete; ready for start up
2023/06/03 15:48:07 [warn] 1#1: the “user” directive makes sense only if the master process runs with super-user privileges, ignored in /etc/nginx/nginx.conf:2
nginx: [warn] the “user” directive makes sense only if the master process runs with super-user privileges, ignored in /etc/nginx/nginx.conf:2
2023/06/03 15:48:07 [notice] 1#1: using the “epoll” event method
2023/06/03 15:48:07 [notice] 1#1: nginx/1.24.0
2023/06/03 15:48:07 [notice] 1#1: built by gcc 12.2.1 20220924 (Alpine 12.2.1_git20220924-r4)
2023/06/03 15:48:07 [notice] 1#1: OS: Linux 5.10.104-linuxkit
2023/06/03 15:48:07 [notice] 1#1: getrlimit(RLIMIT_NOFILE): 1048576:1048576
2023/06/03 15:48:07 [emerg] 1#1: open() “/var/run/nginx.pid” failed (13: Permission denied)
nginx: [emerg] open() “/var/run/nginx.pid” failed (13: Permission denied)
Search…
Stick to bottom
#### 最终解决方案1:
因为这个项目里有nginx,所以使用了nginx的自带用户,用户组来进行配置了权限,解决此问题
例如下面代码:
…此处省略一些基础代码
此处使用的是nginx自带的非root账号执行授权
RUN touch /var/run/nginx.pid
# && chown -R nginx:nginx /app
# && chmod -R 755 /app
&& chown -R nginx:nginx /var/cache/nginx
&& chown -R nginx:nginx /var/log/nginx
&& chown -R nginx:nginx /etc/nginx/conf.d
&& chown -R nginx:nginx /var/run/nginx.pid
&& chown -R nginx:nginx /usr/share/nginx/html
&& chown -R nginx:nginx /etc/nginx/nginx.conf
这部分代码是delete一些用不到的nginx包
RUN apk del nginx-module-image-filter
&& apk del nginx-module-xslt
&& apk del nginx-module-geoip
&& apk del nginx-module-njs
&& apk del curl
USER nginx
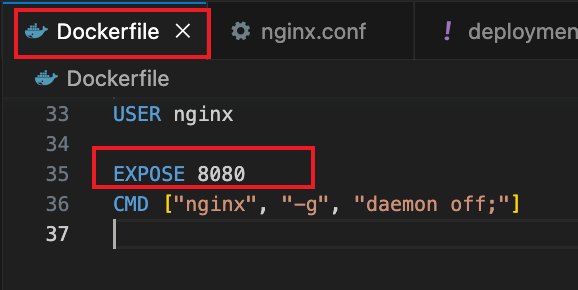
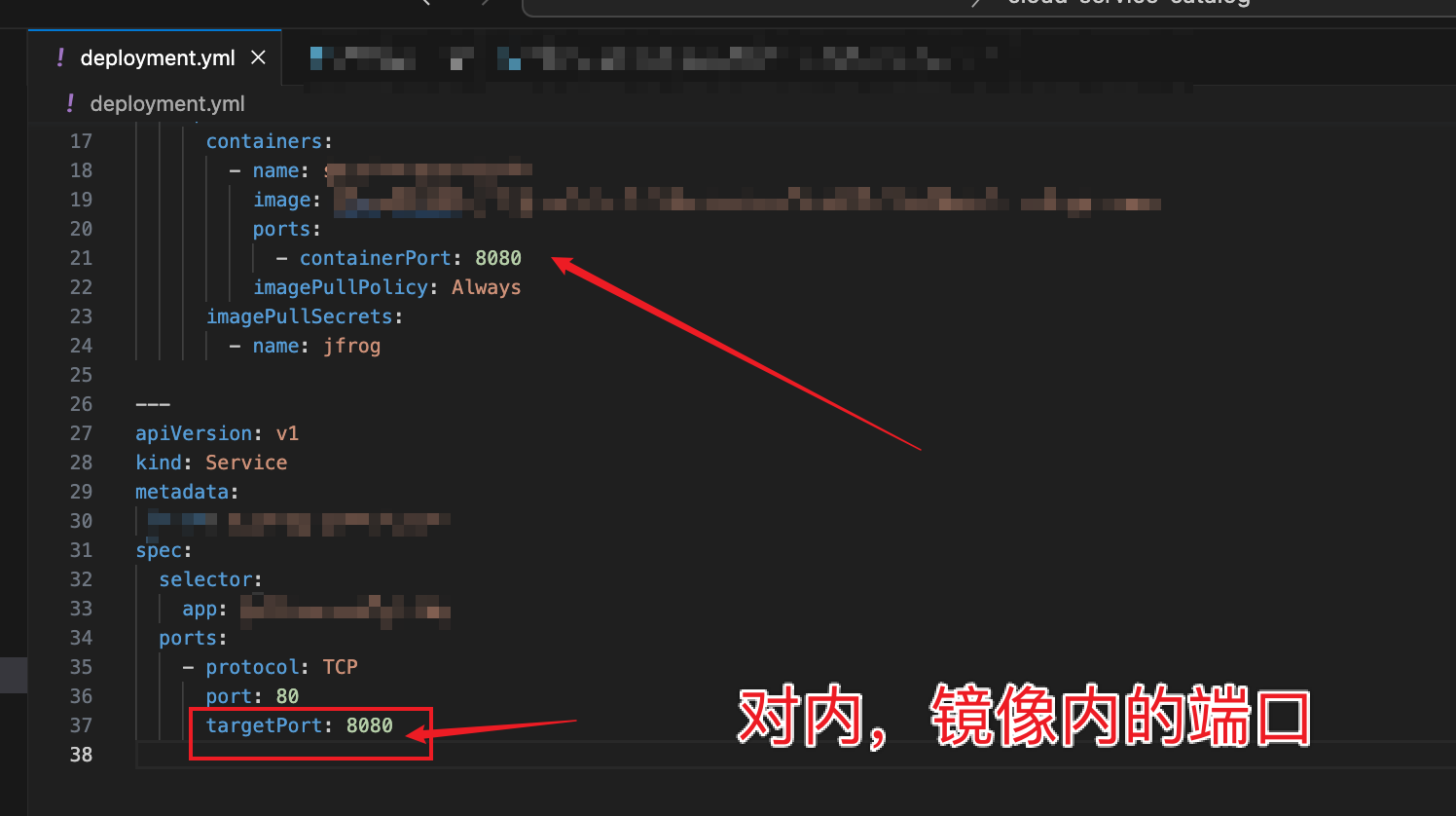
请注意,这里一般不要写80,非root用户容易没有权限绑定80端口
EXPOSE 8080
CMD [“nginx”, “-g”, “daemon off;”]
#### 最终解决方案2:
dockerfile加入下面代码
RUN adduser -D xiaojin
USER xiaojin

k8s yaml 加入下面代码
securityContext:
runAsUser: 0

### 问题3:bind() to 0.0.0.0:80 failed (13: Permission denied)
XXXXXXXX pm2023/06/05 08:04:39 [warn] 1#1: the “user” directive makes sense only if the master process runs with super-user privileges, ignored in /etc/nginx/nginx.conf:2
XXXXXXXX pmnginx: [warn] the “user” directive makes sense only if the master process runs with super-user privileges, ignored in /etc/nginx/nginx.conf:2
Mon, Jun 5 2023 4:04:41 pm2023/06/05 08:04:39 [emerg] 1#1: bind() to 0.0.0.0:80 failed (13: Permission denied)
Mon, Jun 5 2023 4:04:41 pmnginx: [emerg] bind() to 0.0.0.0:80 failed (13: Permission denied)
#### 问题分析:
某些情况下,非Root用户不能绑定1024以下端口,否则会报错:没有权限绑定该端口
#### 问题解决:
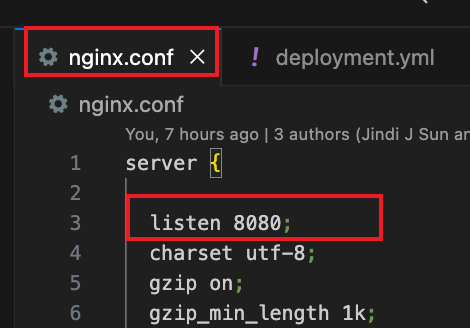
* 修改Dockerfile中的端口配置
* nginx.conf中的端口监听
* k8s.yml中的服务端口暴露配置
* containerPort配置
所有你项目中nginx绑定的都要修改一遍哦~~
代码举例:
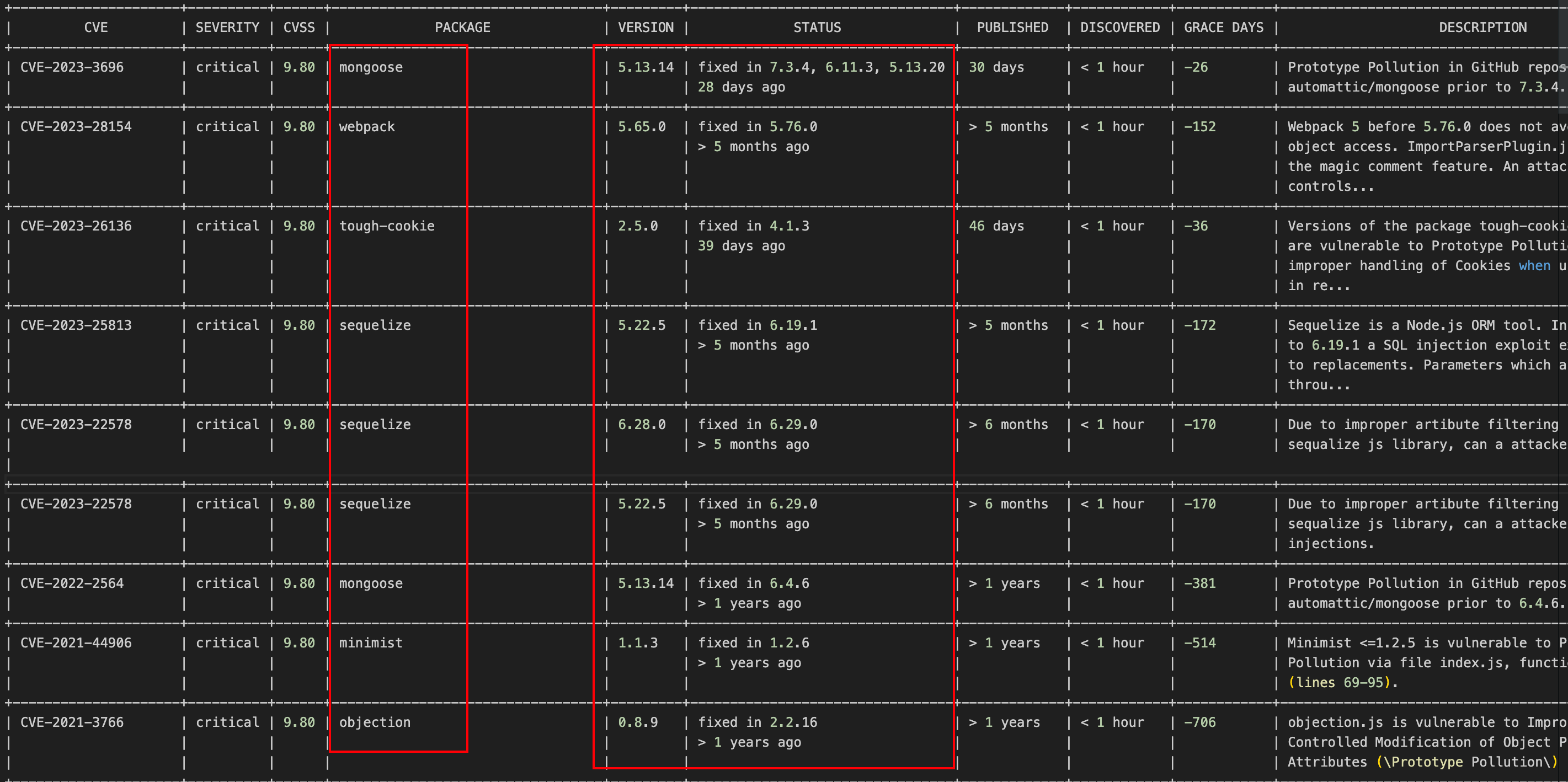
### 问题4:Twistlock扫描Type:javascript
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE | SEVERITY | CVSS | PACKAGE | VERSION | STATUS | PUBLISHED | DISCOVERED | GRACE DAYS | DESCRIPTION | TRIGGERED FAILURE |
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE-2023-3696 | critical | 9.80 | mongoose | 5.13.14 | fixed in 7.3.4, 6.11.3, 5.13.20 | 30 days | < 1 hour | -26 | Prototype Pollution in GitHub repository | Yes |
| | | | | | 28 days ago | | | | automattic/mongoose prior to 7.3.4. | |
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE-2023-28154 | critical | 9.80 | webpack | 5.65.0 | fixed in 5.76.0 | > 5 months | < 1 hour | -152 | Webpack 5 before 5.76.0 does not avoid cross-realm | Yes |
| | | | | | > 5 months ago | | | | object access. ImportParserPlugin.js mishandles | |
| | | | | | | | | | the magic comment feature. An attacker who | |
| | | | | | | | | | controls… | |
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE-2023-26136 | critical | 9.80 | tough-cookie | 2.5.0 | fixed in 4.1.3 | 46 days | < 1 hour | -36 | Versions of the package tough-cookie before 4.1.3 | Yes |
| | | | | | 39 days ago | | | | are vulnerable to Prototype Pollution due to | |
| | | | | | | | | | improper handling of Cookies when using CookieJar | |
| | | | | | | | | | in re… | |
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE-2023-25813 | critical | 9.80 | sequelize | 5.22.5 | fixed in 6.19.1 | > 5 months | < 1 hour | -172 | Sequelize is a Node.js ORM tool. In versions prior | Yes |
| | | | | | > 5 months ago | | | | to 6.19.1 a SQL injection exploit exists related | |
| | | | | | | | | | to replacements. Parameters which are passed | |
| | | | | | | | | | throu… | |
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE-2023-22578 | critical | 9.80 | sequelize | 6.28.0 | fixed in 6.29.0 | > 6 months | < 1 hour | -170 | Due to improper artibute filtering in the | Yes |
| | | | | | > 5 months ago | | | | sequalize js library, can a attacker peform SQL | |
|
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE-2023-22578 | critical | 9.80 | sequelize | 5.22.5 | fixed in 6.29.0 | > 6 months | < 1 hour | -170 | Due to improper artibute filtering in the | Yes |
| | | | | | > 5 months ago | | | | sequalize js library, can a attacker peform SQL | |
| | | | | | | | | | injections. | |
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE-2022-2564 | critical | 9.80 | mongoose | 5.13.14 | fixed in 6.4.6 | > 1 years | < 1 hour | -381 | Prototype Pollution in GitHub repository | Yes |
| | | | | | > 1 years ago | | | | automattic/mongoose prior to 6.4.6. | |
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE-2021-44906 | critical | 9.80 | minimist | 1.1.3 | fixed in 1.2.6 | > 1 years | < 1 hour | -514 | Minimist <=1.2.5 is vulnerable to Prototype | Yes |
| | | | | | > 1 years ago | | | | Pollution via file index.js, function setKey() | |
| | | | | | | | | | (lines 69-95). | |
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
| CVE-2021-3766 | critical | 9.80 | objection | 0.8.9 | fixed in 2.2.16 | > 1 years | < 1 hour | -706 | objection.js is vulnerable to Improperly | Yes |
| | | | | | > 1 years ago | | | | Controlled Modification of Object Prototype | |
| | | | | | | | | | Attributes (\Prototype Pollution) | |
±--------------------±---------±-----±---------------------------------±--------±--------------------------------±------------±-----------±-----------±---------------------------------------------------±------------------+
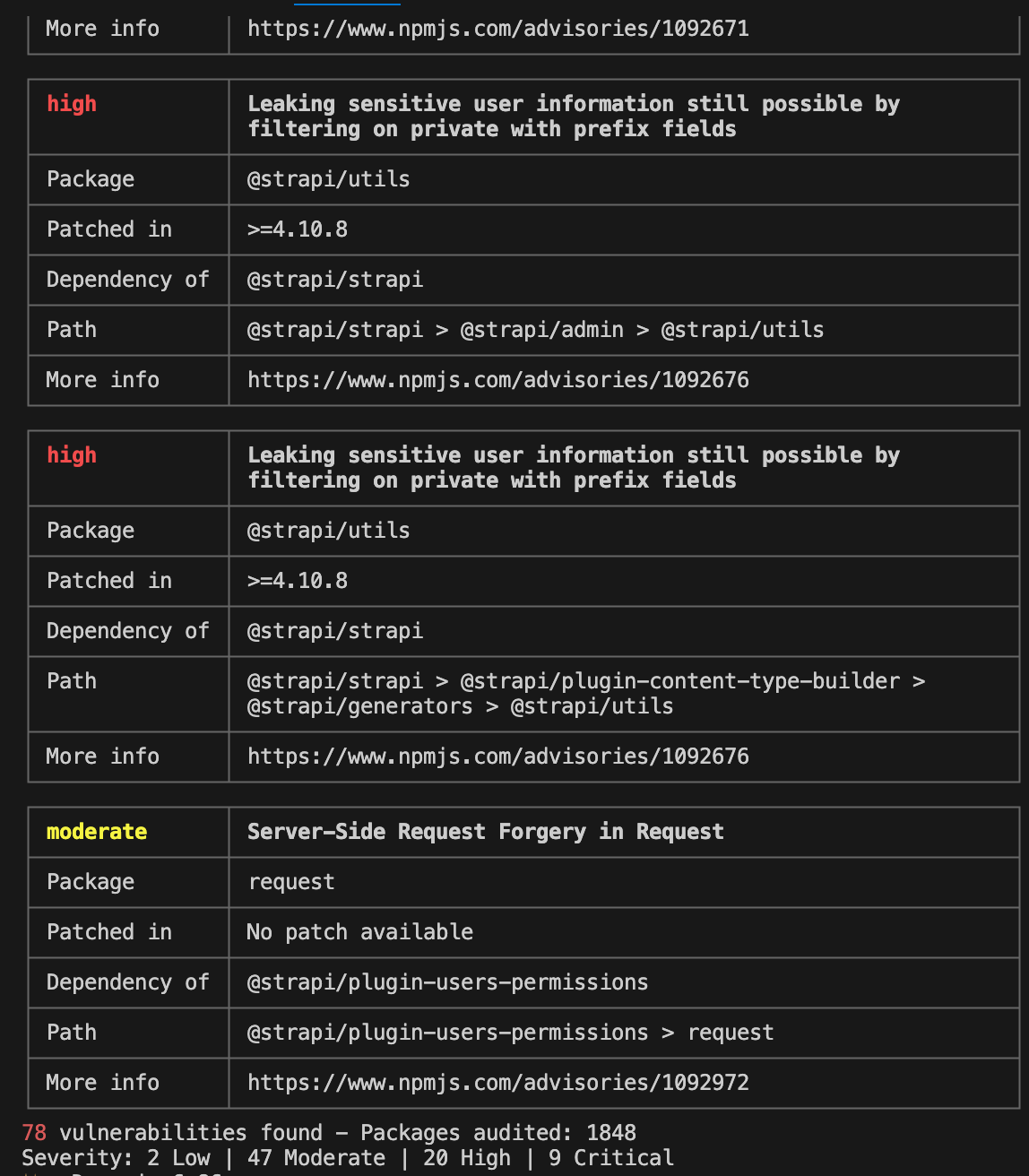
#### 解决方案
##### 打开代码,如果我们在npm 源下,执行 npm audit,会展示该漏洞的信息
* npm audit 返回的漏洞数据来源于 [Github Advisory Database]( )
* 关于 npm audit 详细解释,可以打开我的这篇文档
npm audit
或
yarn audit
##### 查看漏洞检查结果
┌───────────────┬──────────────────────────────────────────────────────────────┐
│ high │ Leaking sensitive user information still possible by │
│ │ filtering on private with prefix fields │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Package │ @strapi/utils │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Patched in │ >=4.10.8 │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Dependency of │ @strapi/strapi │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Path │ @strapi/strapi > @strapi/admin > @strapi/utils │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ More info │ https://www.npmjs.com/advisories/1092676 │
└───────────────┴──────────────────────────────────────────────────────────────┘
┌───────────────┬──────────────────────────────────────────────────────────────┐
│ high │ Leaking sensitive user information still possible by │
│ │ filtering on private with prefix fields │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Package │ @strapi/utils │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Patched in │ >=4.10.8 │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Dependency of │ @strapi/strapi │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Path │ @strapi/strapi > @strapi/plugin-content-type-builder > │
│ │ @strapi/generators > @strapi/utils │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ More info │ https://www.npmjs.com/advisories/1092676 │
└───────────────┴──────────────────────────────────────────────────────────────┘
┌───────────────┬──────────────────────────────────────────────────────────────┐
│ moderate │ Server-Side Request Forgery in Request │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Package │ request │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Patched in │ No patch available │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Dependency of │ @strapi/plugin-users-permissions │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Path │ @strapi/plugin-users-permissions > request │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ More info │ https://www.npmjs.com/advisories/1092972 │
└───────────────┴──────────────────────────────────────────────────────────────┘
78 vulnerabilities found - Packages audited: 1848
Severity: 2 Low | 47 Moderate | 20 High | 9 Critical
✨ Done in 6.86s.
##### 修复漏洞
扫描项目漏洞把不安全的依赖项自动更新到兼容性版本
npm audit fix
### 问题5:npm audit 报错 npm WARN audit 501 Method Not Implemented
npm WARN audit 501 Method Not Implemented - POST https://registry.npmmirror.com/-/npm/v1/security/audits/quick - [NOT_IMPLEMENTED] /-/npm/v1/security/audits/quick not implemented yet
{
error: ‘[NOT_IMPLEMENTED] /-/npm/v1/security/audits/quick not implemented yet’
给大家的福利
零基础入门
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。

同时每个成长路线对应的板块都有配套的视频提供:

因篇幅有限,仅展示部分资料
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
需要这份系统化的资料的朋友,可以添加V获取:vip204888 (备注网络安全)

一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
的板块都有配套的视频提供:

因篇幅有限,仅展示部分资料
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
需要这份系统化的资料的朋友,可以添加V获取:vip204888 (备注网络安全)
[外链图片转存中…(img-aZ6hXQcv-1713323302256)]
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!